The FCC Received 3.7 Million Net Neutrality Comments
#

A new smartphone system may help law enforcement respond faster to school shootings or other emergencies. SchoolGuard is an app with a button that, when pushed, alerts all police officers within a 20-mile radius of the school at risk.Many school districts have police notification systems in place in case of an active shooter or other emergency situation, but in many cases, police or other responders do not get to the scene in time to prevent further casualties. A study from the Department of Homeland Security showed that while the average mass shooting lasted 12.5 minutes, the average response time was 18 minutes.
The increase in school shootings over the years prompted Nate McVicker, a police officer and co-founder of SchoolGuard, to take action. Along with Mike Snyder, a retired Illinois State Police colonel, and a few programmers, McVicker launched SchoolGuard in May of this year.
About 12,000 police officers in all 50 states have downloaded the app since its inception, Vicker told Mashable. Additionally, 60 schools in five states — Indiana, Illinois, Missouri, New Jersey and Texas — have adopted the program. McVicker expects 300 to 400 more schools to introduce SchoolGuard over the next few months.
“We wanted to get as many officers on board as possible,” he said. “Now, we’re starting to roll out to the schools.”
Unlike a traditional panic button, SchoolGuard operates using a smartphone or tablet. Unlike a traditional panic button, SchoolGuard operates using a smartphone or tablet. It’s also more effective than a traditional police radio, Snyder said, since the app alerts both on- and off-duty officers in the affected area.
SchoolGuard App Is a Panic Button That Alerts All Police Within 20 Miles.
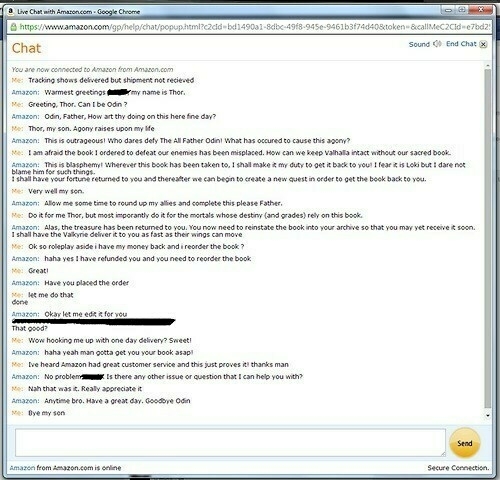
Don’t give me any ideas ^_^
Wow, you learn something new everyday. I’ve just found out about two variations on virtualisation. Linux Containers (LXC) and Vagrant.
Linux Containers (LXC) is known as OS-level virtualisation, meaning the kernel looks after the virtualisation, and there is no need for some extra management software along the lines of VMWare or Virtualbox. The guest OSes run as containers, similar to chroot jails, and all containers, including the main one you booted from, share the same kernel and resources as your main container. As such, LXC only supports linux-based guest OSes. You can’t (easily, anyway) run Windows under LXC. Homepage, Wikipedia.
Vagrant is a strange one. It sells itself as being a way to keep development environments consistent, and I can understand why – if you have a team of people all with a VM of the same OS, but end with different results because they have tinkered with the settings on the VM OS, Vagrant prevents this by keeping the core one in the cloud, and each time the machine is started up, it checks itself against the cloud version, updating itself if needed. That guarantees consistency. Homepage, Wikipedia.
I haven’t tried both of these tools in great detail yet, but here’s some related links for you to check out:
I didn’t realise Wordpress tracks shares of my posts. Some interesting stats.
Turns out the most shared post is this one:
And the most popular share site is Pinterest (654 shares). Least popular share site is Tumblr (574 shares)
This is a Google Developers episode detailing how best to avoid releasing broken or defective games on Google Play. It speaks of three release stages: Alpha, Beta, and Canary/Staged Rollout. Alpha and Beta, almost all people are aware of. But Canary/Staged Rollout is a new term for me, but makes a lot of sense.
If you develop and/or release software, this is probably worth a watch.
A useful snippet of DOS Batch Scripting to get yesterday’s date (or any other historical date for that matter). Very useful to then use with other DOS commands like xcopy or forfiles.
Linux though, it’s a hell of a lot user, just add options to the find command
@echo off
set yyyy=
set $tok=1-3
for /f “tokens=1 delims=.:/-, " %%u in (‘date /t’) do set $d1=%%u
if “%$d1:~0,1%” GTR “9” set $tok=2-4
for /f “tokens=%$tok% delims=.:/-, " %%u in (‘date /t’) do (
for /f “skip=1 tokens=2-4 delims=/-,().” %%x in (‘echo.^|date’) do (
set %%x=%%u
set %%y=%%v
set %%z=%%w
set $d1=
set $tok=))
if “%yyyy%"==”” set yyyy=%yy%
if /I %yyyy% LSS 100 set /A yyyy=2000 + 1%yyyy% - 100
set CurDate=%mm%/%dd%/%yyyy%
set dayCnt=%1
if “%dayCnt%"==”” set dayCnt=1
REM Substract your days here
set /A dd=1%dd% - 100 - %dayCnt%
set /A mm=1%mm% - 100
:CHKDAY
if /I %dd% GTR 0 goto DONE
set /A mm=%mm% - 1
if /I %mm% GTR 0 goto ADJUSTDAY
set /A mm=12
set /A yyyy=%yyyy% - 1
:ADJUSTDAY
if %mm%==1 goto SET31
if %mm%==2 goto LEAPCHK
if %mm%==3 goto SET31
if %mm%==4 goto SET30
if %mm%==5 goto SET31
if %mm%==6 goto SET30
if %mm%==7 goto SET31
if %mm%==8 goto SET31
if %mm%==9 goto SET30
if %mm%==10 goto SET31
if %mm%==11 goto SET30
REM ** Month 12 falls through
:SET31
set /A dd=31 + %dd%
goto CHKDAY
:SET30
set /A dd=30 + %dd%
goto CHKDAY
:LEAPCHK
set /A tt=%yyyy% %% 4
if not %tt%==0 goto SET28
set /A tt=%yyyy% %% 100
if not %tt%==0 goto SET29
set /A tt=%yyyy% %% 400
if %tt%==0 goto SET29
:SET28
set /A dd=28 + %dd%
goto CHKDAY
:SET29
set /A dd=29 + %dd%
goto CHKDAY
:DONE
if /I %mm% LSS 10 set mm=0%mm%
if /I %dd% LSS 10 set dd=0%dd%
REM Set IIS and AWS date variables
set IISDT=%yyyy:~2,2%%mm%%dd%
set AWSDT=%yyyy%-%mm%-%dd%
I’ve been tinkering with Second Life and Spotify on Linux, and discovered there’s a known bug in XDG whereby it complains when you try to access a custom protocol link (e.g. secondlife:// or spotify://) that is already registered within XDG. There’s a (rather cumbersome) way of getting around it, if you’re using Chromium (probably works with Chrome, but I haven’t tried it) First step, add a mime desktop entry - usually in ~/.local/share/application/. This entry must contain a MimeType entry, and a NoDisplay entry. Use the %u to pass the url. This desktop entry will NOT be visible on the menus, and is solely to “connect” to the application you want to invoke when the link is clicked. This example is using the Singularity viewer as an example.
[Desktop Entry] Name=Singularity Comment=Client for Online Virtual Worlds, such as Second Life Exec=~/.singularity-install/handle_secondlifeprotocol.sh %u Icon=~/.singularity-install/singularity_icon.png Terminal=false Type=Application Categories=Application;Network; StartupNotify=true X-Desktop-File-Install-Version=3.0 MimeType=x-scheme-handler/x-secondlife-url NoDisplay=true
Next, inside the program you are calling, you may need to do some manipulation of the passed URL as it will come with escapes (e.g. %20 = space). See later in the post for an example
Finally, make Chromium aware of this new handler, by editing the Chromium preferences, found in (for the Default user), in ~/.config/chromium/Default/Preferences. Chromium must be closed for this to work, or you will lose your changes. In the Preferences file, add this block of code:
"custom_handlers": {
"enabled": true,
"ignored_protocol_handlers": [ ],
"registered_protocol_handlers": [ {
"default": true,
"protocol": "secondlife",
"title": "Second Life",
"url": "x-secondlife-url:%s"
} ]
},
Note the trailing comma, and the url must be prefixed with the mime type you declared in the desktop entry. Start up Chromium afterwards, then click the link. When you click on the link, Chromium gets the link, finds there is a custom handler (in Preferences file), passes it to the mime desktop link you created (which contains the mime type), finds the program to use from the desktop link, and passes the url to the program using the arguments you specified.
Here’s an example of what I mean by manipulating of the passed URL. This is the script from the Firestorm Viewer. Singularity uses a VERY similar script so the code should be nearly interchangeable. I have hacked this script (changes I have made are in bold) so that it works with SLURLs (Second Life URLs) with both spaces, and prefixed with “app/region”
#!/bin/bash
URL="$1"
NEWURL=$(echo $URL| perl -pe ’s/^x-secondlife-url://; tr/+/ /; s/%([a-fA-F0-9]{2,2})/chr(hex($1))/eg;')
URL=echo $NEWURL | sed ’s/secondlife:////g' | sed ’s//app/region///g'
if [ -z “$URL” ]; then
#echo Usage: $0 secondlife://…
echo “Usage: $0 [ secondlife:// | hop:// ] …”
exit
fi
RUN_PATH=dirname “$0” || echo .
#cd “${RUN_PATH}/.."
cd “${RUN_PATH}"
#exec ./firestorm -url '"${URL}"'
if [ pidof do-not-directly-run-firestorm-bin ]; then
exec dbus-send –type=method_call –dest=com.secondlife.ViewerAppAPIService /com/secondlife/ViewerAppAPI com.secondlife.ViewerAppAPI.GoSLURL string:$URL
else
exec ../firestorm -url $URL
fi
I doubt there are many servers out there that can beat this uptime:



Tech lies we all fall for
Interestingly, the last one caught my attention. Here’s the main description:
Recently two members of Team T3 did the same half marathon using the same training plan with the same app. They trained twice together and noticed one of them was recording about a mile less than the other each time. There was no way to test who was being short-changed in their preparation until race day, when one of them hadn’t done enough training and nearly died in the last couple of miles. Lesson: don’t trust apps, trust watches.
“Don’t trust apps, trust watches”? I kind of expected that. After all, a phone is not built to be used as a GPS receiver (even though it is a function), whereas a GPS watch is designed for that function. I have run with the Nike+ app and my SportWatch on at the same time, and have noticed a difference of around 0.2 to 0.25 km between the two. Most of the time the app clocks up more mileage than the watch, but I trust the watch more because it is a dedicated GPS receiver.
Are you still on Facebook? Take a read of this guy's experience, who setup shop on FB back in 2007.
Why I quit Facebook and we are sharing much more than you think | LinkedIn.
Ever wondered how a Computer programmer’s mind thinks?
Apparently, the most sought after language is Java. Not that surprising considering it powers quite a few things, including Android and anything running Android (well, to a point, I guess since it doesn't run Java in the same way that you would run the JVM on, say, your desktop.) Still, gives me a reason to brush up on it. And perhaps work towards a Java certification. I did have J2CP, but that was years ago, so I'm not sure if it is even valid any more.
Although it surprises me a little that Ruby and Perl aren't on this list.
The Top Programming Languages, Ranked by Job Demand, Popularity, More.
Some ecryptfs sites for reference, in reference to previous post.
In particular, use of the Private directory is the simplest setup as it encrypts stuff inside a known folder, leaving it in a scrambled state when you are not logged in, so that no-one can get at it.
If you only need access to those files on an occasional basis, then using the mount option is better.
With the NSA spying scandal, all eyes are on ways to stop the surveillance and protect privacy. Campaigns such as Reset the Net have been used to encourage and push sites and people to amp up their security methods. Disasters such as Heartbleed shows what happens if security is compromised, whether intentionally or accidentally
I used to use TrueCrypt to allocate a virtual hard disk and put my private files in that. One of the benefits of this was that TrueCrypt also supported full disk encryption and Plausible Deniability (e.g. hiding an OS within another OS). However, one of the most frustrating parts of TrueCrypt is that you allocate space and any space you do not use is lost. e.g. if you allocate 10GB, but use only 1GB, there is still 9GB left that allocated to the TrueCrypt volume, but cannot be used by the unencrypted space.
Unfortunately, I recently found out that TrueCrypt shut down, under very suspicious and mysterious circumstances. (check the related articles section below). Sure, you could use LUKS instead, or VeraCrypt (but I haven’t tried VeraCrypt), but considering I only want to encrypt a subset of my files, and not the whole partition, that might be a little overkill.
So, I investigated the ecryptfs. Details can be found on the Wikipedia page, but in short, it allows you to mount directories (it comes with a wrapper to the mount command), but unlike other mount wrappers, you are allowed to mount on top of the same directory. In other words, you can do:
sudo mount.ecryptfs ~/SecuredData ~/SecuredData
And this will take the data stored in the directory and transparently decrypt it when you try to access the directory.
If you copy data into the directory, ecrypt will encrypt it and store it in the underlying directory in an encrypted manner. When you unmount the directory, only the encrypted data is visible. If you combine the mounting process with the optional Filename Encryption, then all you see are files with garbled filenames.
ecrypt supports various encryption methods, from AES and Blowfish, to 3DES and Twofish. Obviously, the higher you choose the encryption level, the slower the access. 3DES encryption resulted in a transfer rate of 7MB/s for me, when copying to the encrypted space, and AES was 16MB/s, so balance your requirement of high encryption vs slow access.
Feedly has gone down again, as a result of another DDoS
7:26am PST: We are currently being targeted by a second DDoS attack and are working with our service providers to mitigate the issue.As with yesterday’s attack, your data is safe. We apologize for the inconvenience and will update this blog post as more information is available or the situation changes.
Denial of service attack (part 2) | Building Feedly.
Could this be a sign of an exodus away from Windows-based environments? The cost of having to upgrade many machines to Windows 7 or Windows 8, not to mention support and licensing, or the premium support cost required to continue supporting Windows XP would not go down well at any sensible company’s finance/accounting department.
Linux is free, open-sourced (see this link for a video explanation of what the term “open-sourced” means), and if a user doesn’t like how it works, they can add/remove or tweak it completely to their liking. They can even build their own kernel to handle bespoke hardware if they wished.
It should be noted that HP teamed up with Bell Labs in the past (who developed the original UNIX OS, on which Linux was inspired from), and built HP-UX (source here), so it isn’t like HP haven’t got some *nix-like environment already under the hood. In fact, WebOS (now looked after by LG, but originally developed by Palm, which was then acquired by HP, then sold to LG) was Linux-based (source here).
HP, which was actually one of Microsoft's key partners in the last decade, is trying to move away from Windows in a move that would clearly turn the company into a direct competitor for the Redmond-based software giant.
HP Stabs Microsoft in the Back: Dumps Windows, Prepares Linux-Based Operating System.
Feedly is up now, but some sites still haven’t updated their articles yet:
Popular note-taking app Evernote and RSS reader Feedly have been hit with major cyberattacks as hackers demand ransom from the latter site to get it back online.Both Evernote and Feedly, two services that work together, confirmed they suffered DDoS (distributed denial of service) attacks, a type of cybercrime that kicks sites offline and is meant to disrupt usage (not steal user data). But Feedly, which is still down, detailed in a blog post that hackers are holding the site up for ransom. It’s unknown as of now if the cyber criminals asked for ransom from Evernote too.
Feedly is being hit by a DDoS. Feedly was touted as the replacement to Google Reader when Google decided to pull the plug on it. And a lot of people moved over to Feedly as a result. I was one of them.
Criminals are attacking feedly with a distributed denial of service attack (DDoS). The attacker is trying to extort us money to make it stop. We refused to give in and are working with our network providers to mitigate the attack as best as we can.We are working in parallel with other victims of the same group and with law enforcement.
We want to apologize for the inconvenience. Please know that you data is safe and you will be able to re-access your feedly as soon as the attack is neutralized
A quick snippet for syncing your date and time via NTP. I have noticed that Windows and Linux do not follow the same convention by standard, and are always an hour out from each other, even though both claim to follow the same time zone. So, what I am having to do is sync via NTP each time I dual boot.
In Linux, this can be done using cron jobs or using the NTP daemon, but that does not do it frequently enough for my liking. So here is a bash snippet for it:
sudo service ntp stop
sudo ntpdate 0.ubuntu.pool.ntp.org 1.ubuntu.pool.ntp.org 2.ubuntu.pool.ntp.org 3.ubuntu.pool.ntp.org 0.uk.pool.ntp.org 1.uk.pool.ntp.org 2.uk.pool.ntp.org 3.uk.pool.ntp.org ntp.ubuntu.com
sudo service ntp start
The first line stops the NTP daemon, since the ntpdate command does not like it when it is running (port in use). The second command uses a server in the selected list to sync with. The final line restarts the NTP daemon.
The Windows (Windows 7) equivalent is very similar. Like with linux, it has an in-built sync facility, but it again does not sync often enough for my liking. Like with the bash script, the commands must be run with elevated rights, so you must “Run as Administrator”, or run from an elevated rights command prompt, which you do as follows:
net stop “Windows Time”
net start “Windows Time”
w32tm /config /manualpeerlist:“0.ubuntu.pool.ntp.org 1.ubuntu.pool.ntp.org 2.ubuntu.pool.ntp.org 3.ubuntu.pool.ntp.org 0.uk.pool.ntp.org 1.uk.pool.ntp.org 2.uk.pool.ntp.org 3.uk.pool.ntp.org ntp.ubuntu.com” /syncfromflags:ALL /update
w32tm /resync
This code starts/restarts the Windows Time service then configures it with a pool of NTP servers, before asking the service to update itself and then resync. The resync action is what adjusts the time.

Owners of iPhones and iPads have been targeted by a hacker who is freezing iOS devices and demanding a ransom of up to £55 to unlock them.
The majority of the attacks have taken place in Australia although there are also reports of Britons being affected.
The Information Commissioner’s Office (ICO) has criticised the Student Loans Company Limited after a series of data breaches involving customers’ records.
The business reported several incidents where information held about customers, including medical details and a psychological assessment, had been sent to the wrong people.
An ICO investigation found that not enough checks were carried out when documents were being scanned to add to customer accounts, and more sensitive documents actually received fewer checks.